Microsoft Azure - System administration
Cloud Computing
If your website is running on an old server that is slow and unreliable, you’ll need a solution that is fast, accessible, and resilient during peak traffic times. Cloud computing offers an ideal solution in such scenarios.
Cloud services operate on a consumption-based model, meaning your company will only pay for the resources it actually uses nothing more, nothing less. Furthermore, cloud computing enhances predictability in budgeting and billing by basing costs on actual usage.
If the website experiences high traffic peaks, scalability is just a click away. Beyond scalability, there are several other benefits to moving to the cloud. But Cloud doesn't only solve issue, it offers also potential benefit to innovate and lead in their industry.
Cloud Models
Depending on your needs, there are three different models of cloud computing, each offering unique benefits and considerations.
Private
A company that requires full control over its data and resources, direct management of installation and maintenance of its equipment, and a distinct, secure environment will prefer to use a Private Cloud. With a Private Cloud, all resources are exclusively dedicated to the company, without the need to share with other organisations. This solution can be quite costly and complex.
Public
If owning and maintaining your own data center for your resources and data is too expensive for your company, or if you lack the necessary staff to manage such a complex infrastructure, you can opt for a provider like Microsoft Azure. Their team will handle all equipment maintenance, and you only pay for the resources you use. Furthermore, deploying and scaling your infrastructure can be accomplished in just a few clicks. Your company will only need an access to Internet, and you just have to subscribe to a provider. Additionally, while the resources are shared with other organisations, your data remains private and secure.
Hybrid
As the name suggests, a Hybrid Cloud is a combination of Public and Private Cloud. For instance, if your company wants to maintain full control over sensitive data and keep it off the Public Cloud, it can set up a secure Private Cloud environment. Meanwhile, for other needs such as deploying and scaling applications quickly a Public Cloud solution can be utilised. The primary advantage of this approach is its flexibility.
Financial Models
There are two different financial models for cloud computing. The financial strategy used for a Private Cloud is, of course, different from that of a Public Cloud.
Capital Expenditure
Capital Expenditure (CapEx) refers to an initial investment. As explained earlier for the Private Cloud, the company must purchase all the equipment necessary to set up its own data center. While this can be very expensive upfront, over the long term, it can be beneficial, potentially saving money after several years.
Operational Expenditure
Operational Expenditure (OpEx), on the other hand, follows a consumption-based financial model where the more you use, the more you pay. Billing is immediate, and you have significant flexibility regarding resource usage. While it might cost more in the long run compared to a Private Cloud, it’s important to remember that maintaining your own data center involves ongoing costs for upgrading and replacing equipment, which can be expensive.
Benefits
There are several benefits of the Cloud :
- High Availability : geographically distributed data centers. If one data center goes offline, traffic is automatically redirected to another through load balancing mechanisms, ensuring continued operation. This redundancy enhances reliability. This level of availability is not typically achievable with a private cloud setup or with isolated measures like having multiple network lines or redundant power supplies alone.
- Scalability : With the Cloud, you can immediately scale your server resources without the need to procure additional hardware (e.g., RAM or CPU) or schedule intervention for hardware installation. The Cloud offers two types of scalability :
- Vertical Scalability: increasing the resources (e.g., CPU, RAM) of your existing server.
- Horizontal Scalability: adding more machines to distribute the workload.
- Predictability : Imagine you are setting up your own data center, but you miscalculate the required resources, leading to performance issues, or too many, resulting in unnecessary costs. Additionally, if a server lacks the performance to handle high traffic during a major event, your website might crash. All of these challenges can be avoided with the Cloud which allows you to dynamically adjust resources in real-time.
- Governance : Maintaining a uniform data center, ensuring all machines are operational, performing physical hardware maintenance, applying software updates, and guaranteeing data protection require significant effort, diligence, and can be quite expensive. Public Cloud services can handle these tasks for you.
- Elasticity : This concept combines the principles of Predictability and Scalability. With elasticity, you can automatically scale your resources as needed, and costs will adjust accordingly. For instance, if your website experiences a traffic spike during a special event, you can temporarily increase resources for that specific period without worrying about manual intervention or scheduling.
- Reliability : If one server becomes inaccessible, it won't be a problem because you will be automatically redirected to another one, with no noticeable difference. Additionally, your data is protected from risks like fire or hardware failure, thanks to backup solutions. Finally, you don't have to worry about incident recovery, as it is fast and handled by an IT team responsible for ensuring smooth operations.
- Security : Network security, data encryption, identity management, and threat detection are easily managed in the Cloud. Security is crucial for customers, as they need to trust that their data and systems are protected.
- Manageability : A central monitoring system exists to track resource usage, costs, and automate performance tuning. It consolidates all the information about your data center in one place, ensuring a seamless and efficient overview.
Cloud Service Types
There is three different types of Cloud services.
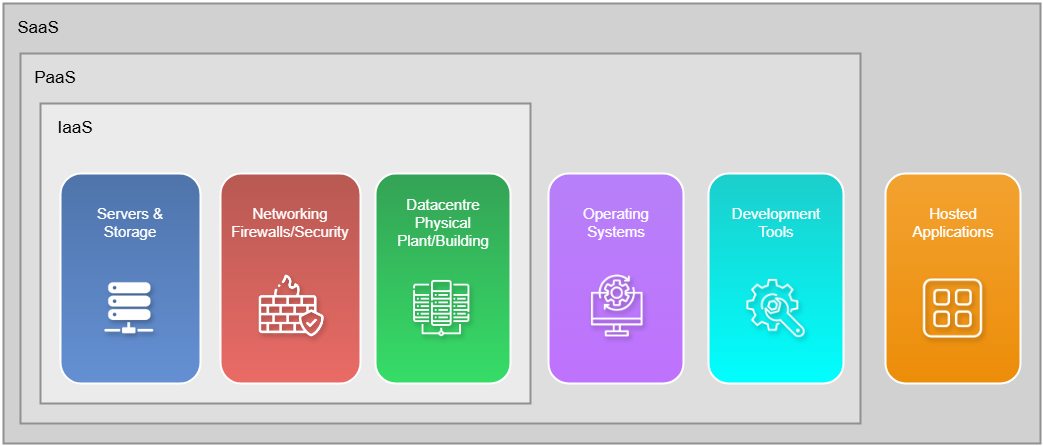
Infrastructure as a Service
Infrastructure as a Service (IaaS) provides raw infrastructure on the cloud, including servers, storage, and networking, giving you full control over it. It's similar to owning land, where you can build anything you want on top.
For example, if you have an application running on an on-premises server, you can set up the server, storage, and network on your IaaS platform and migrate your data. It will function the same way as it does on your on-premises setup.
The advantages of IaaS are in flexibility, scalability and reliability. You can simply rent a server with the required storage, without having to worry about the infrastructure. Additionally, IaaS offers scalability benefits, you can upgrade or downgrade your resources whenever needed, and you'll only pay for what you use. Finally, cloud providers offer robust uptime guarantees, ensuring that your IaaS will remain reliable at all times.
For example on Azure, an virtual machine is considered as a IaaS.
Plateform as a Service
Platform as a Service (PaaS) is primarily used by developers. The main purpose of PaaS is to provide an infrastructure, operating system, and all the necessary features for an application to run, all pre-installed. Developers only need to execute their code, and everything should work seamlessly. This is different from IaaS, where you have to install and configure everything yourself.
PaaS includes not only servers, storage, and networking but also operating systems and development tools. For example, on Azure, you don't need to worry about updating the operating system or managing tools like Python. Microsoft handles those tasks, allowing you to focus solely on developing your code.
Software as a Service
Software as a Service (SaaS) refers to software that is hosted and managed by a service provider. Users can subscribe to the service and access it over the internet. Examples of SaaS include platforms like Netflix and Google Drive.
With Infrastructure as a Service (IaaS), you are responsible for installing and configuring the operating system and networking components on the provided infrastructure.
Platform as a Service (PaaS) allows you to focus solely on running your code, as the cloud provider handles everything else, such as infrastructure and runtime environments.
Finally, with SaaS, you don’t need to manage or configure anything; you simply subscribe to and use the service.
Microsoft Azure
Architectural Components
Understand the fundamentals of Azure architectural components.
Regions, Availability and Compliance
The main purpose of Regions and Availability Zones is to enable the deployment of solutions that remain accessible to customers worldwide without latency.
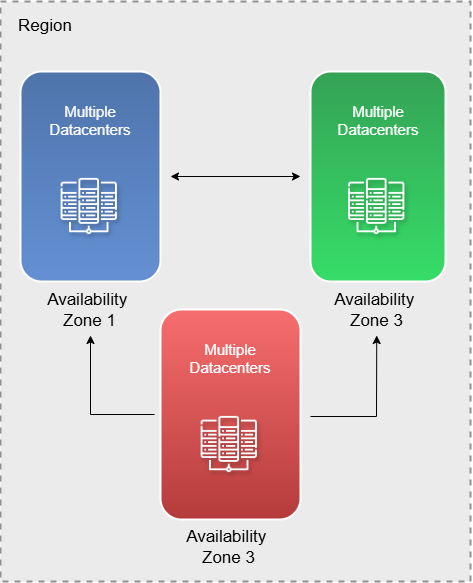
Regions
An Azure Region consists of multiple data centers located across the globe, actually 60 regions and 140 countries. With new data centers being added in various regions every year, Azure global infrastructure continues to grow. To see all regions and countries available on Azure, click here.
These globally distributed data centers ensure that Azure provides high scalability, flexibility, and robust disaster recovery solutions.
Another important aspect involves data residency and user proximity. You can choose to store your data in a specific Azure region to comply with your country's data protection laws and regulations.
Finally, keep in mind that not all Azure services are available in every region. Therefore, it's essential to check regional service availability during deployment planning. This helps ensure your application is optimised for both performance and compliance.
Availability Zones
Each Azure region consists of multiple avaialability zone. And each availability zone, consists of multiple datacenters and these are physically separated from one another. This separation forms the foundation of Availability Zones. In the event of a power outage or network failure in one zone, the other zones remain operational, ensuring continued availability.
All data centers within a region are also interconnected through high-speed networks, which guarantees high availability of services.
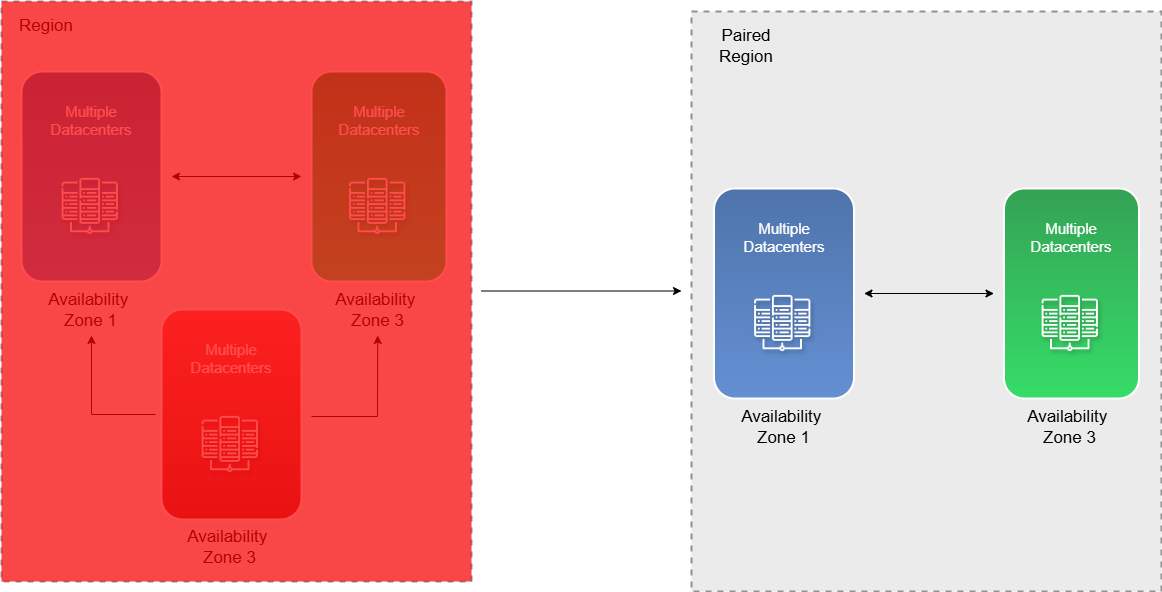
Disaster Recovery
In the rare case where all Availability Zones in a region fail, the entire region becomes inaccessible. To handle this, Azure provides a secondary region, known as a paired region, which automatically takes over to ensure service continuity. This paired region is predefined by Microsoft and typically located at least 300 miles (about 480 km) away to ensure geographic separation, high availability, and resilience against large-scale failures.
To further protect your data, Azure offers automated replication for certain services. This means your data is automatically copied to the paired region, ensuring that up-to-date backups are available and your applications remain reliable and recoverable in case of outages.
If you have data residency requirements and have initially restricted your data to a single region (ex. West Europe), and that region experiences a complete outage, the paired region will still be located within Europe. This is because Azure ensures that data replication and failover comply with GDPR and other EU data protection regulations.
Sovereign Regulations
Sovereign regulations are national laws that govern how data must be stored, processed, and accessed within a specific country. These regulations are particularly important for industries like government, healthcare, and finance, where data privacy, sovereignty, and compliance are critical.
To address these needs, Azure provides sovereign cloud environments that are physically and logically separated from the global Azure infrastructure. These environments are designed to meet strict national requirements and are often operated by local entities.
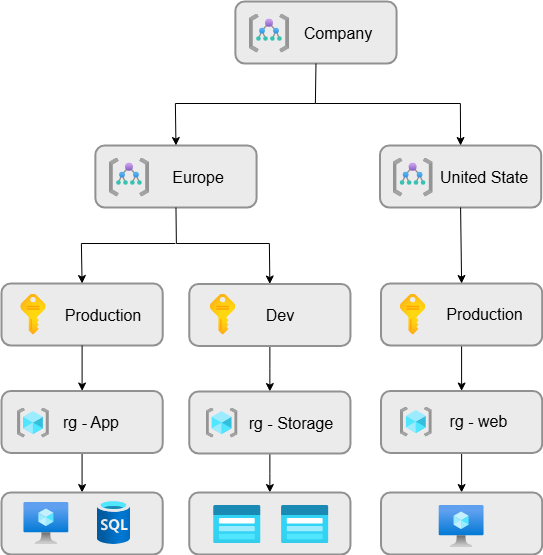
Resource Organisation
One of the basic components of Azure is Azure Resources (such as Virtual Machines, Storage Accounts, Virtual Networks, etc.). Bellow, here is the realted features to Azure Ressource.
Resource Groups
These resources can be grouped into Resource Groups, which act as a box to organise and manage related resources. Resource Groups help simplify billing, management, and support easier provisioning.
Additionally, Resource Groups allow you to deliver services to your customer base with reduced latency by deploying them in specific regions. This is also useful for data sovereignty requirements or accessing region-specific services.
You can move resources from one Resource Group to another without any disruption to the service. Furthermore, you can easily scale the services running within your Resource Groups without any issues.
Careful, if a resource group is deleted, all of the resources will be deleted.
Subscriptions
To create resources and Resource Groups in Azure, you need a Subscription. A Subscription allows you, and any users you’ve granted access, to deploy resources such as Virtual Machines, Storage Accounts, and more.
Each Subscription also serves as a billing boundary, helping you track your usage and costs. This enables you to see exactly what you're spending and where.
Within this billing boundary, there is also an access control boundary, which allows you to manage permissions. You can define who has access to what, and what actions they can perform within your Azure environment.
Management Groups
If you have multiple Subscriptions, you can create Management Groups to organise them.
This simplifies how you apply governance policies across your Azure environment. When you assign a policy or condition to a Management Group, it is inherited by all the Subscriptions under that group.
Here’s an example of a complete hierarchy for a company in Azure :
Ressources
There are different compute types available depending on what you need to deploy for your infrastructure.
Virtual Machines
Deploying a Virtual Machine on Azure gives you access to a wide range of VM sizes, allowing you to customise specifications such as CPU, memory, storage, and operating system. You can easily scale your VM up or down based on your needs, which impacts cost efficiency, you only pay for what you use. Your VMs are backed by Azure’s robust infrastructure, ensuring high levels of security and reliability.
In terms of networking, you can configure a public endpoint, allowing your VM to be accessible from the internet, or a private endpoint, which keeps the VM within a secure internal network. Additionally, Virtual Network Peering enables communication between two VMs located in different virtual networks, allowing them to work together seamlessly.
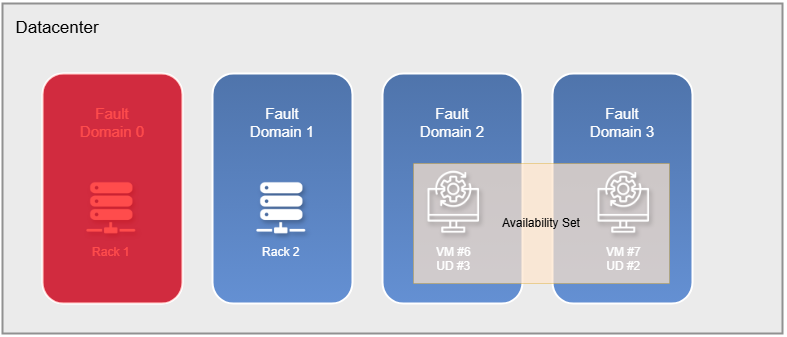
Availability Sets
Availability Sets are a feature in Azure designed to ensure that your virtual machines remain available during both planned and unplanned maintenance events. This is achieved through two core concepts :
- Fault Domain (FD): A fault domain is a group of physical hardware that shares a common power source, network switch, and cooling system. It protects against hardware failures. Azure data centers typically have multiple fault domains, so if one fails, your VMs in another fault domain will remain unaffected. Each Azure data center generally provides up to three fault domains.
- Update Domain (UD): An update domain is a logical group used to manage maintenance operations. When Azure performs planned maintenance, updates are applied to one update domain at a time. This ensures that not all VMs are rebooted or impacted simultaneously. VMs in different update domains will not be updated at the same time, allowing your application to remain available during updates.
For higher availability, you can also deploy your virtual machines across Availability Zones, which are physically separate locations within a region. This provides even greater protection against datacenter-level failures.
To sum up, Availability Sets improve availability, are considered a best practice, and are simple to implement.
Scale Set
Azure Virtual Machine Scale Set is a service that allows you to deploy and manage a group of identical, load-balanced VMs. It helps you automatically scale the number of virtual machines based on demand, making your application more resilient and cost-effective.
It’s designed for applications that need to be highly available and scalable, for example, web servers accessed by large numbers of users.
Virtual Desktops
Virtual Desktop operates on the same principle as Remote Desktop Services (RDS). It allows you to connect to your Azure Virtual Desktop (AVD) from any computer, giving you access to your applications and data from anywhere.
Multiple users can use AVD simultaneously without requiring a specific license. You can also join these machines to your domain, and they function just like corporate devices.
The key difference between a Virtual Machine (VM) and AVD is that VMs are typically used to host applications and services, whereas AVD provides a full desktop experience for end users.
AVD is cost-effective, it' optimises expenses as it doesn't require a dedicated license, making it an economical choice.
App Services
Azure App Services is a Platform as a Service (PaaS) solution that supports multiple programming languages and frameworks, including Python, .NET Core, Java, and more. It is DevOps-optimised, allowing seamless integration with tools like Azure DevOps, GitHub, Docker Hub, and others. Additionally, it offers easy scalability, enabling you to scale your application up or down based on demand.
For developers, App Services is a more efficient choice than using a Virtual Machine (VM). Unlike Infrastructure as a Service (IaaS), with App Services you don't need to manage the operating system, runtime, or infrastructure, just focus on your application code.
Container Services
It's important to understand the concept of containerisation.
You don’t need to worry about managing the server, operating system, or container runtime, Azure handles all of that for you. All you have to do is deploy your container and your application.
Container Instances
Azure Container Instances (ACI) is a PaaS container service that allows you to run containers without managing any virtual machines.
It offers a fast and simple deployment experience, making it ideal for lightweight or short-lived workloads. You can customise resource allocation with flexible sizing options, including CPU, memory, and other settings to fit your application’s needs.
It's an ideal solution for simple applications that need fast and efficient execution, or for task automation and build jobs. It will cost per second.
Container Apps
Azure Container Apps builds on the foundation of Azure Container Instances, adding features that support more complex applications. The main difference between the two is that Azure Container Instances is intended for running a single container without orchestration, while Azure Container Apps is designed to handle orchestration and multiple containers. It also supports microservices architectures.
With Azure Container Apps, you can easily scale your containers based on demand, including scaling to zero when not in use. It also integrates smoothly with DevOps tools and CI/CD pipelines, making it easier to manage deployments and updates. You will pay per app and usage.
Kubernetes Service (AKS)
Azure Kubernetes Service (AKS) is designed for applications that require more complex orchestration, auto-scaling, and high availability.
Using AKS involves more management effort, as you need to handle multiple nodes, monitor the cluster’s health, and ensure you're running the latest supported version of Kubernetes.
Despite the added complexity, AKS integrates smoothly with DevOps tools and CI/CD pipelines, making it well-suited for production-grade workloads. You pay per nodes and usage.
More informations about Kubernetes here.
Functions
Azure Functions are used to execute code and return results, supporting multiple programming languages to meet your application’s real-time needs. This service is designed to integrate seamlessly with other Azure resources.
One of its key benefits is automatic scalability, if your application receives a high number of requests, Azure Functions will scale to handle the load. You only pay per execution, so there are no charges when your code isn't running. This model is known as FaaS (Function as a Service). Azure Functions abstracts away the underlying infrastructure, allowing you to focus solely on your code without worrying about servers or runtime environments.
Virtual Networking
Azure Virtual Networking functions much like a traditional on-premises network. It allows you to isolate and segment your network resources, for example, by creating multiple subnets. You can customise your network topology, which can be secured using Network Security Groups (NSGs), Application Security Groups (ASGs), and Azure Firewall.
All Azure resources can be managed through the Virtual Network (VNet). You have control over inbound and outbound traffic to and from the internet, for instance, for your virtual machines. Additionally, you can establish connectivity between Azure and your on-premises environment, which is covered in more detail under VPN Gateway.
VPN Gateway
The primary purpose of Azure VPN Gateway is to enable encrypted traffic between your Azure Virtual Network and your on-premises datacenter. It acts as a secure bridge between the two environments by establishing a VPN tunnel. This tunnel ensures that communication between your Azure resources and on-premises infrastructure is both private and secure.
To sum up, VPN Gateway offers both Site-to-Site and Point-to-Site VPN options. The Site-to-Site VPN as been explained above, while the Point-to-Site VPN allows individual users, such as remote employees, to securely connect to Azure resources from anywhere over the internet.
Additionally, VPN Gateway can be easily scaled based on your bandwidth and performance requirements, ensuring it meets the needs of both small and large-scale deployments.
Express Route
Azure ExpressRoute is a service that provides a private connection between your on-premises infrastructure and Azure datacenters, bypassing the public internet. Because it’s a private connection, it offers higher reliability, faster speeds, and enhanced security compared to traditional internet-based connections.
ExpressRoute isn't limited to Azure alone, it can also be used to connect to other Microsoft cloud services, such as Microsoft 365 and Dynamics 365.
Domain Name System
Azure DNS is a global service, meaning it is not restricted to a specific region. DNS queries are answered by the nearest available server, ensuring optimal performance and low latency. It offers a secure and reliable solution for managing your domain names, with the ability to easily scale as your needs grow.
Azure DNS provides seamless integration with the Azure platform. You can manage custom domains and update DNS records directly from the Azure portal, with changes being applied automatically, eliminating the need for manual intervention or additional configuration.
Stack
Storage
Understand the fundamentals of storage in Azure.
Accounts
An Azure Storage Account is essentially a cloud-based account where you can store various types of data. It offers multiple services depending on the type of data you want to store.
You have several storage options, such as blob storage, file storage, queue storage, table storage, etc.
One of the main advantages of an Azure Storage Account is its high durability and availability. Your data is replicated to protect against outages and data loss. Additionally, your data is secure, Azure provides features such as encryption in transit and at rest, along with access control mechanisms.
You can easily scale your storage as your application grows, and access it from anywhere with the appropriate permissions. It also integrates seamlessly with other Azure resources and third-party applications.
Redundancy
Redundancy is used to ensure that your data is replicated and stored in multiple locations to improve availability and protect against data loss. Azure offers several redundancy options :
- Locally Redundant Storage (LRS) : Data is replicated within 1 datacenter, in 1 region, across 3 fault domains. Durability : 99.999999999% (11 nines).
- Zone-Redundant Storage (ZRS) : Data is replicated across 3 availability zones (3 separate datacenters) within 1 region, across 3 fault domains. Durability : 99.9999999999% (12 nines).
- Geo-Redundant Storage (GRS): Data is replicated in the primary region, within 1 datacenter, across 3 fault domains, and asynchronously copied to a secondary region, also in 1 datacenter with 3 fault domains. Durability : 99.99999999999999% (16 nines).
- Geo-Zone-Redundant Storage (GZRS): Data is replicated across 3 availability zones (3 datacenters) in the primary region, across 3 fault domains, and asynchronously replicated to 1 datacenter in a secondary region across 3 fault domains. Durability : 99.99999999999999% (16 nines).
Services
With Azure Storage Services, you have multiple service avaible such as :
- Blob Storage : Used for unstructured data like images, videos, and other media files ;
- Disk Storage : Used for Virtual Machines, providing high performance and reliability. Choose for example between SSD or HDD options based on your performance and cost requirements ;
- Queue Storage : Used for message queuing between components of an application ;
- File Storage : Ideal for managing file shares, similar to a traditional file server ;
- Table Storage : A NoSQL key-value store for structured, non-relational data.
All of them, except Disk Storage, which is dedicated to Virtual Machines, can be easily accessed through a public endpoint to perform API calls and retrieve data. The endpoint typically follows this format :
- https://<storage-account-name>.<service>.core.windows.net
Access Tiers
Access tiers in Azure define how frequently you need to access your stored data for Blob. The choice of tier depends also on four main factors : how often the data is accessed, the minimum storage duration (before beeing deleted), the access costs (read & write), and the storage costs.
- Hot : Best for data that needs to be accessed frequently. It has low access costs, no minimum storage duration, but higher storage costs ;
- Cool : Designed for infrequently accessed data. It has higher access costs, lower storage costs, and a minimum storage duration of 30 days ;
- Cold : For rarely accessed data, it has moderate access costs, low storage costs, and a minimum storage duration of 30 days ;
- Archive : Ideal for long-term storage of data you rarely access. It offers the lowest storage cost, but has high access and retrieval costs, with long retrieval times (can take hours). The minimum storage duration is 180 days.
The main benefit of Azure access tiers is cost management, you can choose between performance and price the tier that fits your access needs. It’s flexible, allowing you to easily switch between tiers as your data usage changes. Plus, your data is stored with high durability and reliability, ensuring it's safe no matter which tier you use.
Also lifecycle management policies in Azure Storage can be used to automate the transition of data to the most cost-effective access tier based on how frequently the data is accessed and how long it's stored.
Migrate
Azure Migrate is a tool that helps companies transition their infrastructure from on-premises environments or other cloud providers to Microsoft Azure.
It analyses the entire infrastructure and provides recommendations on what needs to be changed or updated before migrating to the cloud. For example, some operating systems may not be supported on Azure, and the tool will flag these issues in advance.
Azure Migrate supports a wide range of migration scenarios, including databases, servers, web applications, and more. For highly specific or complex migrations, it integrates with other Microsoft services and partner tools to ensure a smooth and seamless transition.
Databox
Azure Data Box is a service that helps you securely transfer large amounts of data to Azure Storage and compute services.
It’s especially useful when you need to move terabytes of data from your on-premises infrastructure to the cloud. Transferring such volumes over the internet can be slow and insecure, especially if the data is sensitive. Azure Data Box enables efficient and secure large-scale data transfers.
The Data Box solution involves a physical device provided by Microsoft. Instead of sending data over the internet, you connect the device directly to your data center, load the data onto it offline, and then ship it back to Microsoft. Once received, Azure uploads the data to your cloud storage.
To ensure security, all data stored on the device is encrypted. This means even if there's an issue during shipment, your data remains protected.
There are three different types of Azure Data Box, each designed for different data transfer needs :
- Data Box Disk : Portable SSD disks, ideal for smaller data loads (up to a few terabytes) ;
- Data Box : A rugged, tamper-resistant device suited for transferring larger volumes of data (up to 80 TB) ;
- Data Box Heavy : Designed for very large-scale data transfers, supporting up to 1 PB of data.
File Mangement Options
While Azure Data Box is ideal for transferring very large volumes of data, there are other file management options better suited for smaller data transfers. These tools support both command-line and graphical interfaces :
- AzCopy : A command-line utility designed to transfer data to and from Azure Storage. It's ideal for backup, archiving, and large-scale operations. AzCopy supports scriptable operations and can also be used to move data between Azure and other cloud providers ;
- Azure Storage Explorer : A graphical user interface (GUI) tool for managing Azure Storage resources. It allows you to view, upload, download, and manage data stored in Azure, and supports a wide range of storage types such as Blob, File, Queue, and Table storage.
- Azure File Sync : This service syncs files between your on-premises Windows Server and Azure File Shares. It’s particularly useful when you need to retain local access to files while ensuring they are backed up or accessible via the cloud.
Identity, Acces and Security
Understand the fundamentals of identity, acces and security in Azure.
Entra ID
Microsoft Entra ID (formerly Azure Active Directory) is a comprehensive identity and access management service. It provides secure user identity management and access policy control for organisations. Here is some key features :
- Single Sign-On (SSO) : When you try to log in to a Microsoft service such as the Azure Portal, Outlook, or Exchange, you must authenticate using a user account that exists in your Entra ID. As an identity provider, Entra ID verifies and validates your credentials to ensure you are the authorised user ;
- Application Management : Supports integration of third-party (non-Microsoft) applications to allow single sign-on (SSO) using Microsoft Entra ID credentials ;
- Device Management : Allows you to register and manage devices in the organisation, enforce compliance policies, and control access to applications and resources based on the device's status and domain membership.
- Multi-Factor Authentication (MFA) ;
- Conditional Access ;
- B2B & B2C Collaboration ;
- Role-Based Access Control (RBAC) ;
To sum up, Microsoft Entra ID is fully managed by Azure. You simply need to integrate your applications and manage your users, especially if you're not using external identity providers. It provides a robust security framework with features like MFA, Conditional Access, and device compliance. Additionally, it scales easily, as you add more users, resources, or devices, the system automatically adapts to support them.
Authentication and Authorisation
There is a main difference between authentication and authorisation :
- Authentication : Confirms who you are, verifying your identity using methods such as passwords, tokens, or biometrics ;
- Authorisation : Determines what you are allowed to do, involving settings like user roles, access controls, and permissions.
In Azure, authentication is handled by Microsoft Entra ID, which verifies the identity of users and services. On the other hand, authorisation is enforced through Role-Based Access Control (RBAC), Azure policies, and access control rules, which determine what actions a user or service is allowed to perform within the environment.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) enhances security by requiring multiple forms of verification before granting access, for example, a one-time password (OTP) sent to a mobile device, or others solutions like biometrics, phone call, etc.
Indeed, depending on a password is not very safe. If the password is compromise, anyone could gain access to your account.
Conditional Access
Conditional Access on Azure allows you to create policies that grant or block access to specific applications based on conditions such as :
- User and Group : Restrict access to an application to specific users or groups only.
- Location : Restrict access based on geographic location, for example, block access from outside the office.
- Device Compliance : Check the security and compliance of your device before granting access. For instance, access may be denied if your device lacks antivirus protection or is not a corporate-approved device.
- Risk Level : Analyse your usual behavior to establish a usage pattern. If suspicious activity is detected, such as unusual login times or locations, access to the application may be blocked.
All of these features offer benefits such as protecting sensitive data, securing remote work, and ensuring BYOD (Bring Your Own Device) security by making sure users access applications only from their professional or compliant devices.
External Identities
There is two differents type of external identities : B2B and B2C
B2B
Enables organisations to invite external users without creating full internal accounts (e.g., no mailbox or internal license required). These users authenticate using their own credentials, reducing account management overhead.
They will then appear in Microsoft Entra ID as external users, allowing you to manage their permissions and grant access to specific resources. For example, you can provide access by adding them to a group.
This helps improve collaboration on shared projects between two companies and allows you to grant access to specific applications or resources as needed.
B2C
When connecting to certain applications, users can log in using accounts like iCloud, Google, and others. This type of authentication is known as B2C (Business-to-Consumer).
B2C is designed for your customers who want to access your application using their personal accounts, such as an iCloud or Facebook account.
You can also implement a form of multi-factor authentication (MFA) by sending a one-time password (OTP) to the user’s email address to approve the connection. The B2C feature enhances the user experience by allowing users to easily create and log in to their accounts, making it simple to access e-commerce platforms, gaming services, or social media.
Role Based Access Control (RBAC)
Role-Based Access Control (RBAC) is used to define permissions for users or groups, specifying who can do what, where, and with which Azure resources. To implement this, you create a Role Assignment.
RBAC follows an inheritance model: if you assign a role at the management group level, the permissions will automatically apply to all subscriptions, resource groups, and resources beneath it. You can define access at any level of the resource hierarchy.
RBAC is especially useful in multi-user environments or large organisations where access needs to be restricted. It also helps in securing sensitive projects by limiting access only to authorized users.
Entra Domain Services
In a traditional on-premises infrastructure, you can deploy Active Directory Domain Services, where you manage users, machines, Group Policy Objects (GPOs), and more, and where you need to deploy and maintain a domain controller. With Microsoft Entra Domain Services, you don't have to worry about the domain controller, as it is fully managed by Microsoft. You simply join your machines to the domain and start using the services.
You can also apply Group Policies to devices to enforce rules, such as restricting non-corporate usage on company-managed machines.
Similar to traditional Active Directory Domain Services, Microsoft Entra Domain Services supports LDAP and Kerberos authentication, which are essential for legacy applications. This is important because Microsoft Entra ID uses modern authentication protocols by default, such as OpenID Connect and OAuth 2.0, which are not compatible with many legacy systems.
Zero Trust
The principle of Zero Trust means that nothing is trusted by default, every access request must be fully verified before it is granted. In other words, access is denied unless the system can confirm that the user is authorized and all security conditions are met.
First, a global evaluation is performed based on factors such as user identity, location, device health, and workload. Then, user access is restricted to the minimum necessary to perform their tasks (least privilege access). Additionally, users and devices are segmented within the network, sessions are encrypted, and the system uses analytics and threat detection tools to continuously monitor and respond to risks.
Defense in Depth
Security in Azure is structured in multiple layers to minimise the risk of attackers reaching sensitive data. Each layer plays a specific role in building a strong defense-in-depth strategy. Here are the layers, in order :
- Physical Security : Azure data centers and hardware are physically protected to prevent unauthorised access. Only authorized personnel can enter these facilities.
- Identity and Access Management : Access is controlled through services like Azure Active Directory (Azure AD) and Role-Based Access Control (RBAC), ensuring users and groups only have the permissions they need.
- Perimeter Security : This includes firewalls, DDoS protection, and other tools that protect against external attacks at the network edge.
- Network Security : Network segmentation and security groups are used to control and monitor traffic flow within the Azure environment.
- Compute Security : Protects virtual machines, containers, and other compute resources from unauthorised access or compromise.
- Application Security : Focuses on securing applications against external threats, such as code injection, vulnerabilities, or misconfigurations.
- Data Protection : Ensures that data is protected at rest and in transit using encryption, backups, and access policies.
Each of these layers can be implemented and managed using Azure services and resources, forming a comprehensive and resilient security posture.
Defender for Cloud
Microsoft Defender for Cloud is a security solution designed not only for Azure resources but also for other cloud providers and your on-premises infrastructure. It also supports integration with remote repositories such as GitLab, Azure DevOps, GitHub, and more to provide security recommendations.
Today, maintaining a dedicated security team can be costly. That's why Microsoft Defender offers a comprehensive security platform with a centralised management panel to consolidate issues and deliver actionable recommendations to enhance your security posture.
Defender continuously monitors your infrastructure and provides a security score, similar to an audit, with detailed feedback to help you improve your environment. It also acts as a compliance officer, checking against standards such as ISO to ensure your systems meet industry regulations.
Cost Optimisation and Management
Understand the fundamentals about Cost Optimisation and Management in Azure.
Factors Affecting Cost
There are several factors that affect the cost in Azure :
- Type of Resource : Costs vary depending on the type of resource you are using. Each resource has its own metering system that determines consumption. For example, with Virtual Machines (VMs), you are charged based on the number of VMs you have and how long they are running.
- Consumption Model : Azure operates on a Pay-as-you-go model. This means you only pay for what you use. For instance, if your VM is running for only one hour per day and is shut down afterward, you will only be charged for that hour, reducing costs.
- Region : The cost of Azure services can vary based on the region where your resources are deployed. For example, deploying in "Switzerland North" may have different pricing compared to "US West" for the same services.
- Ingress and Egress : Incoming data transfers (Ingress) are free of charge; you only pay for the resources receiving the data. However, outgoing data transfers (Egress) are billed based on the volume of data sent outside of Azure.
- Type of Subscription : Azure offers different subscription types based on your needs. For example, a Dev/Test subscription provides discounted rates. Additionally, if you are a student and can verify your status, Microsoft grants you credits to use on Azure.
Marketplace
The Azure Marketplace is similar to the Google Play Store, where you can find, install, and deploy applications that seamlessly integrate into your Azure architecture.
For example, if you are using Terraform and want to incorporate it into your Azure DevOps pipeline, you can easily install Terraform from the Azure Marketplace and follow the provided instructions to integrate it into your CI/CD pipeline.
The marketplace is filled with a wide range of applications developed not only by Microsoft but also by third-party companies. However, some features and applications may require additional purchases and are consider as prenium dataset.
Careful, if you are installing some services, such as Wordpress, it may automatically deploy ressource that will be charged.
Pricing Calculator
Before to deploy your infrastructure on Azure, you can use the Azure Pricing Calculator in order to estimate the cost of ressources that will be deployed.
It's totally transparency, you can simulate deploying VMs, storage account, network, etc. It helps you to plan your budget and make right decisions.
Then, you can plan your migration to Azure or just do an comparison between other Cloud Provider.
TCO Calculator
The Azure Pricing Calculator helps you estimate the cost of the resources you plan to deploy from scratch. However, if you already have an on-premises infrastructure, you can use the TCO (Total Cost of Ownership) Calculator to evaluate the estimated cost and long-term benefits of migrating to Azure as a cloud solution.
With the TCO Calculator, you can specify the number of databases, servers, storage units, network equipment, and more that currently exist in your on-premises environment. The calculator then provides a detailed estimate of costs and potential savings when migrating to Azure.
Cost Management
Azure Cost Management analyzes and monitors your infrastructure, providing detailed insights into where your money is being spent. It helps you track and manage your budget effectively, enabling you to optimise your investments.
If there are resources that are underutilised or not being used, Cost Management will generate reports highlighting them, allowing you to identify opportunities to reduce costs. You can then decide whether to delete or optimise these resources to save money.^
Resource Tags
If you have a large infrastructure with many resources, it is highly recommended to use tags for efficient management. Tags allow you to categorise resources based on specific attributes, such as department, environment, or project name. This makes it easier to distinguish and filter them in Cost Management for detailed analysis for example.
Additionally, you can automatically apply tags during resource deployment, enabling seamless integration into resource lifecycle automation. This helps streamline management and improve visibility across your Azure environment.
Governance and Compliance
Policies
To comply with industry standards such as ISO 27001, for example, if our company is based on it, we can use Azure Policies to restrict deployments according to the standard. We can define policies that reject the creation of resources if they do not adhere to the requirements specified in those policies.
You can define a policy, assign it to a management group, subscription, or resource group, and then view the compliance status. This allows you to see the percentage of compliance and determine whether further actions are needed to meet the standard.
Azure Policies help ensure that all your resources remain compliant with regulatory standards. They prevent configuration drift and allow you to maintain custom controls across your environment.
Resource Locks
Resource Locks prevent the modification or accidental deletion of resources in Azure by placing a lock at different levels such as the subscription, resource group, or directly on the resource itself. There are two types of resource locks :
- Read-Only Lock : Users can view the resource, but cannot modify or delete it.
- Delete Lock : Users can modify and manage the resource (e.g., start/stop or scale), but cannot delete it.
They ensure that your most vital assets remain untouched and operational.
Service Trust Portal
Before migrating all your resources and data to a cloud provider such as Azure, you should verify that the cloud provider plateform meets your compliance requirements. To support this, Microsoft provides a website that serves as a comprehensive repository of compliance-related information and resources call Service Trust Portal.
You will find compliance reports (such as on-page findings, penetration tests, and assessments), trust documents (explaining how Microsoft maintains security and compliance), as well as compliance guides and white papers. This portal provides a clear overview, compliance support, and a resource hub that can be used by IT professionals, compliance officers, and auditors as a reliable source of guidance on regulatory compliance.
Pureview
Microsoft Purview is a unified data governance service that helps you manage and govern your data across multiple platforms, whether it's stored in Azure, on-premises datacenters, or in SaaS applications.
Purview automatically discovers and classifies your data across your organization using sensitivity labels. It supports data governance by enabling the creation of data policies, managing data access, and implementing data protection measures. It also helps assess compliance with your internal standards and regulatory requirements.
Purview is especially useful for large organizations with data spread across various environments that require strong data protection, compliance, and security management.
Resource Deployment Tools
Deploying and managing resources efficiently and effectively.
Portal, Powershell and Azure CLI
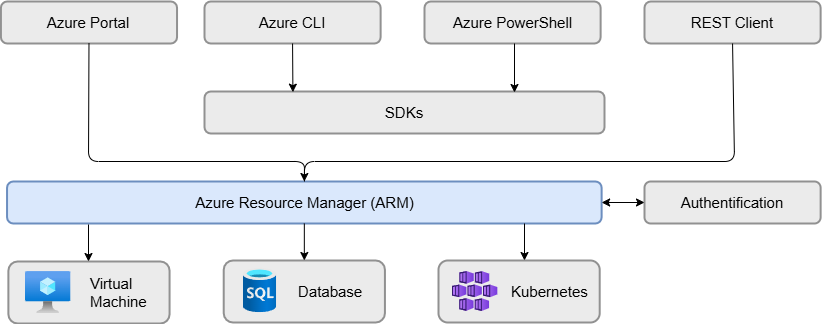
There are four different ways to interact with Azure :
- Azure Portal : The most commonly used interface, it's a web-based, user-friendly platform for managing all Azure services. You can create, manage, and monitor resources through a graphical interface with just a few clicks.
- Azure PowerShell : By using PowerShell command line and importing the Azure module, you gain access to advanced functions for creating and managing resources. This method is ideal for automating complex and repetitive tasks by scripting.
- Azure Cloud Shell : A browser-accessible command-line interface available directly in the Azure Portal. It provides a convenient way to manage Azure resources without installing anything locally.
- Azure CLI : A cross-platform command-line tool, especially suited for Linux users who prefer a Bash-like experience. It allows you to manage Azure resources similarly to PowerShell.
The choice of which tool to use depends on your needs :
- Azure Portal : Best for quick tasks and visual monitoring.
- Azure PowerShell & Azure CLI : Ideal for automation and scripting.
- Azure Cloud Shell : A pre-configured management environment accessible from the browser.
Arc
If you have data and resources running across multiple cloud providers or in your on-premises datacenter, and you want to centralise management through a single platform, Azure Arc is the ideal solution.
All you need to do is install the Azure Arc agent on your machines. Once connected, you can manage those resources directly from the Azure Portal, or via CLI, PowerShell, and other Azure tools.
Azure Arc enables unified management, extends Azure services, and allows you to enforce governance and compliance across all environments. It is especially useful for organisations with hybrid cloud deployments, helping them modernise on-premises infrastructure and manage edge resources more effectively.
Resource Manager
Azure Resource Manager (ARM) is the deployment and management framework that enables you to create, update, and delete resources in your Azure account. Regardless of how you send a request, whether through the Azure Portal, CLI, PowerShell, or SDK, it goes to the backend and is processed by Azure Resource Manager to perform the requested action.
Infrastructure as Code (IaC)
DevOps - Infrastructure as Code
Azure Resource Manager (ARM) provides a solution called ARM templates, which are JSON files that define the infrastructure and configuration of your Azure resources. These templates allow ARM to create, modify, and delete resources in a consistent and repeatable way.
In addition to ARM templates, there are other infrastructure-as-code (IaC) tools available, such as Bicep (a more concise language for Azure) and Terraform (a popular open-source, multi-cloud IaC tool).
Monitoring Tools
Advisor
Aside from the basic Azure documentation that outlines general best practices, there's a tool called Azure Advisor that provides personalised recommendations and best practices tailored to your specific Azure configuration and usage.
It acts like a consultant, analysing all the resources running in your Azure environment. Based on your usage patterns and resource types, Azure Advisor offers recommendations in five key areas :
- High Availability
- Security
- Performance
- Cost Optimization
- Operational Excellence
All recommendations and the monitoring dashboard provided by Azure Advisor are free to use, and you will not be charged for accessing them.
Service Health
Maintenance, patches, upgrades, etc., are dplanned and handled by Microsoft. However, you may still need to plan for potential downtime in your own environment, as these activities can occasionally impact your services. Azure provides tools to help you prepare for and stay informed about any issues affecting your resources. These tools are divided into three components :
- Azure Service Health (Platform-Level) : ongoing issues with Azure services, planned maintenance, health history of services relevant to your environment.
- Azure Resource Health (Resource-Level) : Gives insights into the current and past health status of your individual resources, along with step-by-step troubleshooting guidance or root cause analysis when available.
- Azure Status (Global View) : Offers a real-time, global overview of the health of all Azure services, helping you identify.
These tools are essential for proactive issue management and communication, allowing you to respond quickly to incidents and inform stakeholders effectively.
Monitor
Azure Monitor is a service that collects, analyzes, and acts on telemetry data from both Azure and on-premises infrastructure, by monitoring applications, infrastructure, and network components, including metrics such as CPU, memory, and disk usage for example.
It gathers data from both environments, and you can configure alerts and notifications to improve proactive monitoring. You also have access to customisable dashboards with performance metrics.
Additional Azure services can be integrated with Azure Monitor, such as log Analytics or application Insights, for maintaining the best possible user experience and monitoring application performance
All of this is centralised within Azure Monitor, making it a powerful tool for IT operations, DevOps teams and Infrastructure and application health monitoring.